
Shiba Inu has grown a lot since last year, and its price significantly increased during its first year. The market capitalization of the cryptocurrency Shiba Inu (SHIB) is $6.7 billion. The coin was created by the anonymous user or group known as Ryoshi and is the 14th largest token.
Indian-based cloud security firm ‘ PingSafe’ reported that they discovered a leaked Shiba Inu AWS account credential on a public code repository, which was valid only for two days and later became invalid after their findings.
The leaked AWS credentials severely exposed the company’s data hosted on the Amazon web service.
“Our estimation has the potential to cause serious security breaches, including but not limited to user fund theft, token embezzlement, disruption of services, etc.” -wrote Anand Prakash Founder & CEO, PingSafe
“To protect the integrity of the company and as per our ethical hacking policy, the Pingsafe team did not verify the precise extent of the breach.- he added.
Pingsafe noted the credential was leaked in committing AWS infrastructure keys on a public GitHub repository (now removed) by one of Shiba’s internal developers.
The researcher shared the screenshot of the commit with the hardcoded AWS keys.
 |
| Shiba hardcoded credentials |
To validate the keys, Pingsafe performs the AWS validate credentials request, which confirms the legit of the keys.
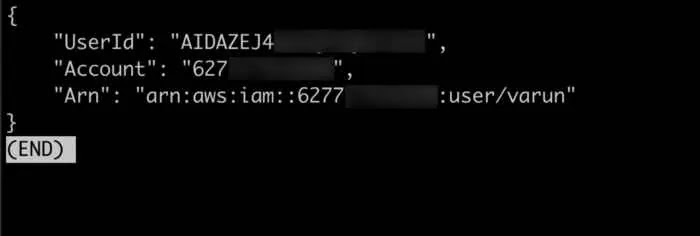 |
| AWS validates credentials request |
Additionally, the research team also perform some basic tests like listing users of AWS accounts, called List Instances API request, that were able to successfully fetch the instances running in the account.
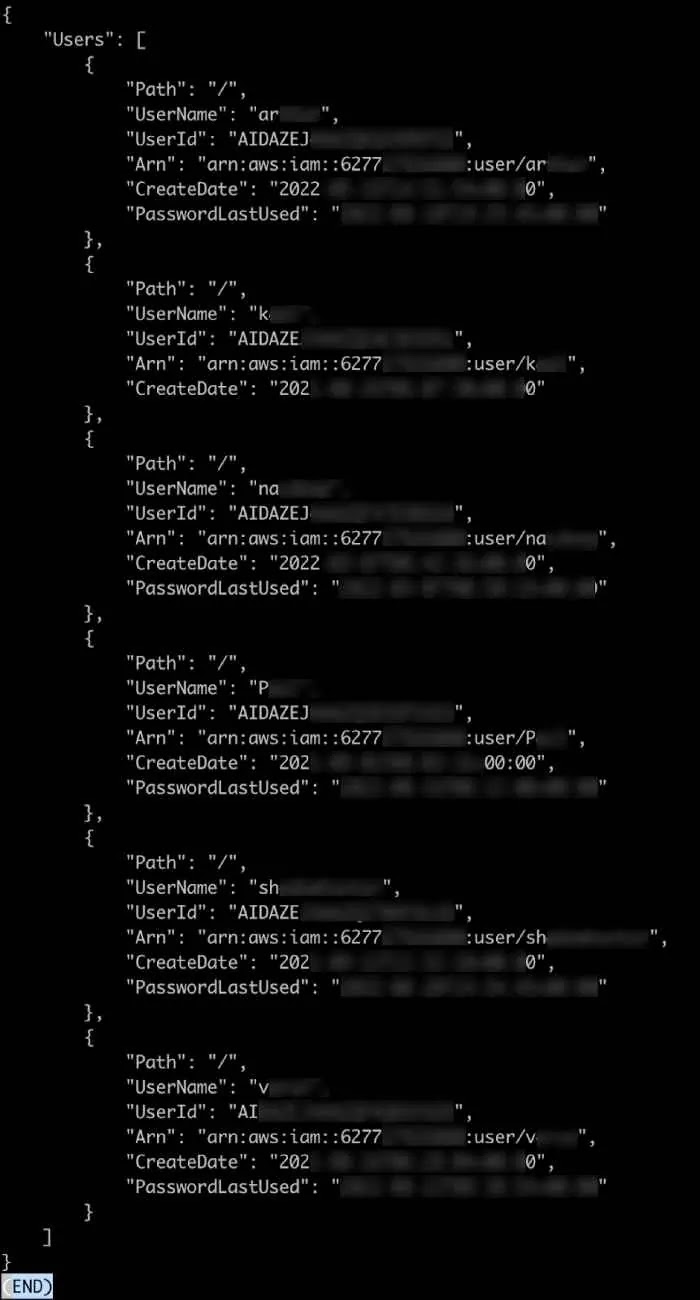 |
| Shiba AWS user’s account |
 |
| Shiba AWS List Instances |
PingSafe tried to contact the Shiba team over Twitter/Telegram but failed to receive any response. Even the developer’s profiles of Shiba were also anonymous, having no public emails.
Earlier also we have seen a number of such issues as leaking credentials on GitHub, and many bug bounty hunters still report such leaking of data.
Also read a report by MDSec labs on the misconfiguration and human error called “NotGitBleed“, which can simply expose important data and may lead to major security breaches.
GitHub has earlier announced it will automatically block accidental secrets exposure to prevent exposure of credentials before committing code to remote repositories.
Regarding the same, Facebook officially joins a partnership with the GitHub team to search and invalidate the Facebook API access tokens that have been accidentally uploaded and leaked inside GitHub repositories.
[Image Credit: PingSafe]